01. How can an administrator apply endpoint policies based on invitation?
a) Create security posture tags.
b) Create separate endpoint profiles.
c) Configure group assignment rules.
d) Configure on-fabric detection rules.
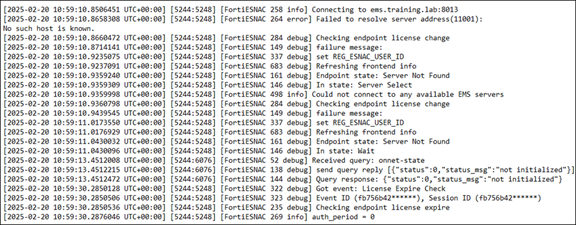
02. Refer to the exhibit.
What is preventing FortiClient from registering with FortiClient EMS?
a) FortiClient could not reach the EMS server FQDN.
b) FortiClient user verification failed.
c) The FortiClient license expired.
d) FortiClient could not connect to the EMS server on port 8013.
03. What is the purpose of a webserver certificate in a FortiClient EMS deployment?
a) It is used by FortiClient Web Filter extension to perform SSL-inspection on web traffic.
b) It is used for telemetry connection from FortiClient to FortiClient EMS.
c) It is used to sign certificate requests from endpoints for zero trust network access (ZTNA).
d) It is used for communication with FortiGate as part of the Security Fabric.
04. Which two authentication methods are used for user verification on FortiClient EMS?
(Choose two.)
a) RADIUS
b) SAML
d) TACACS
05. You are the administrator of VPN infrastructure that is struggling with performance issues due to most of their workforce now working remotely. The security architecture team is evaluating zero trust network access (ZTNA) as a potential replacement for their aging VPN deployment.
In what two ways does ZTNA differ from a conventional VPN?
(Choose two.)
a) More resource intensive
b) Continuous trust check
c) Based on network layer
d) Uses an access proxy
06. An administrator must provide web access to a zero trust network access (ZTNA) server hosted behind FortiGate. Which configuration must the administrator perform to achieve this outcome?
a) Add web server to the ZTNA destinations endpoint profile on FortiClient EMS.
b) Create a standard firewall policy with ZTNA webserver as the destination.
c) Manually install a ZTNA client certificate on the endpoint.
d) Configure a ZTNA server on FortiGate with service HTTPS.
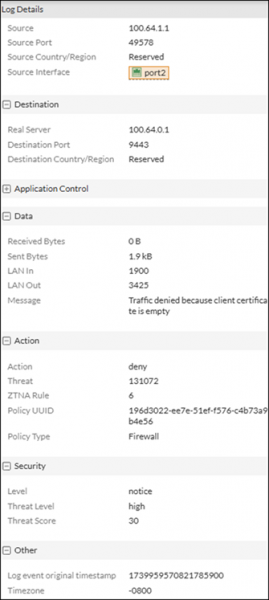
07. Refer to the exhibit.
Why was the traffic denied access to the zero trust network access (ZTNA) server?
a) The endpoint compliance status changed.
b) The FortiClient endpoint did not provide a client certificate.
c) The traffic matched a ZTNA deny policy.
d) The client certificate was revoked.
08. The security team must ensure that it uses the security posture information of an endpoint as part of the dynamic security policies matching criteria.
Which two pieces of information do endpoints provide in telemetry data to fabric devices?
(Choose two.)
a) Resource utilization
b) OS version
c) Vulnerability information
d) Network bandwidth stats
09. Which configuration on FortiGate quarantines the endpoint in a Security Fabric indicator of compromise (IOC) deployment?
a) Active connectors
b) Endpoint profile
c) Playbooks
d) Automation stitch
10. Which two statements about how full privileged access management (PAM) works with FortiClient are correct?
(Choose two.)
a) FortiClient EMS must have the FortiPAM add-on license applied.
b) Privileged access management must be enabled in the system settings endpoint profile.
c) FortiClient installer must have zero trust network access (ZTNA) and FortiPAM features enabled.
d) A FortiPAM standalone agent must be installed on the endpoint.
 Before you write the Fortinet FortiClient EMS Administrator (FCP_FCT_AD-7.4) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Access Service Edge (SASE) (FortiClient EMS Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet FortiClient EMS Administrator (FCP_FCT_AD-7.4) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Access Service Edge (SASE) (FortiClient EMS Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.