01. What is the common feature shared between IPv4 and SD-WAN ECMP algorithms?
a) Both support volume algorithms.
b) Both can be enabled at the same time.
c) Both use the same physical interface load balancing settings.
d) Both control ECMP algorithms.
02. What is eXtended Authentication (XAuth)?
a) It is an IPsec extension that forces remote VPN users to authenticate using their credentials (username and password).
b) It is an IPsec extension that authenticates remote VPN peers using a pre-shared key.
c) It is an IPsec extension that forces remote VPN users to authenticate using their local ID.
d) It is an IPsec extension that authenticates remote VPN peers using digital certificates.
03. Which two statements about incoming and outgoing interfaces in firewall policies are true?
(Choose two.)
a) An incoming interface is mandatory in a firewall policy, but an outgoing interface is optional.
b) A zone can be chosen as the outgoing interface.
c) Multiple interfaces can be selected as incoming and outgoing interfaces.
d) Only the any interface can be chosen as an incoming interface.
04. Which type of traffic inspection requires FortiGate to act as a CA?
a) SSL certificate inspection when protecting multiple clients connecting to multiple servers.
b) SSL traffic inspection when protecting a local SSL server.
c) SSL traffic inspection when protecting multiple clients connecting to multiple servers.
d) SSL certificate inspection when protecting a local SSL server.
05. Which two statements about advanced AD access mode for the FSSO collector, agent are true?
(Choose two.)
a) It supports monitoring of nested groups.
b) It is only supported if DC agents are deployed.
c) FortiGate can act as an LDAP client to configure the group filters.
d) It uses the Windows convention for naming; that is, Domain\Username.
06. Which statement about firewall policy NAT is true?
a) DNAT is not supported.
b) You must configure SNAT for each firewall policy.
c) DNAT can automatically apply to multiple firewall policies, based on DNAT rules.
d) SNAT can automatically apply to multiple firewall policies, based on SNAT policies.
07. Which three settings and protocols can be used to provide secure and restrictive administrative access to FortiGate?
(Choose three.)
a) SSH
b) FortiTelemetry
c) HTTPS
d) Trusted authentication
e) Trusted host
08. Which two statements correctly describe the differences between IPsec main mode and IPsec aggressive mode?
(Choose two.)
a) The first packet of aggressive mode contains the peer ID, while the first packet of main mode does not.
b) Main mode cannot be used for dialup VPNs, while aggressive mode can.
c) Aggressive mode supports XAuth, while main mode does not.
d) Six packets are usually exchanged during main mode, while only three packets are exchanged during aggressive mode.
09. Which two IP pool types are useful for carrier-grade NAT deployments?
(Choose two.)
a) One-to-one
b) Overload
c) Fixed port range
d) Port block allocation
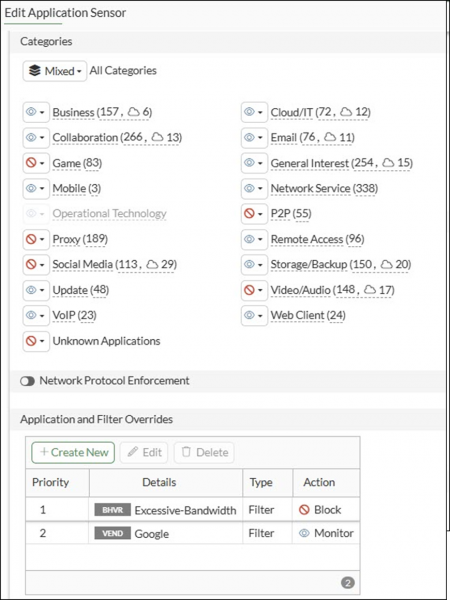
10. Refer to the exhibits.
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits. You cannot access any of the Google applications, but you are able to access www.fortinet.com.
What would you do to resolve this issue?
a) Move up Google in the Application and Filter Overrides section to set its priority to 1.
b) Change Inspection mode to Flow-based.
c) Set SSL inspection to certificate-inspection.
d) Add *Google*.com to the URL category in the security profile.
 Before you write the Fortinet FortiOS Administrator (NSE4_FGT_AD-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Professional - Secure Networking (FortiOS Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet FortiOS Administrator (NSE4_FGT_AD-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Professional - Secure Networking (FortiOS Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.