01. What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in a hub-and-spoke topology?
(Choose two.)
a) It ensures consistent settings between phase1 and phase2.
b) It guides the administrator to use Fortinet recommended settings.
c) It automatically installs IPsec tunnels to every spoke when they are added to the FortiManager ADOM.
d) The VPN monitor tool provides additional statistics for tunnels defined with an IPsec recommended template.
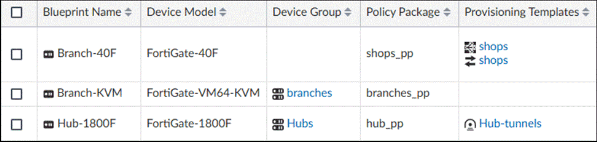
02. Refer to the exhibit.
As a FortiManager administrator, you reviewed the device blueprint configuration. Based on the exhibit, which configuration deviates from best practices?
a) You should assign at least one provisioning template to the Branch-KVM blueprint.
b) You should assign a device group to the Branch-40F blueprint.
c) You should assign a single provisioning template to the Branch-40F blueprint.
d) You should assign a provisioning template or a device group to the Hub-1800F blueprint, but not both.
03. Which of the following step is necessary to use overlay links in SD-WAN?
a) Overlay links must be configured in the global VDOM on a FortiGate.
b) Overlay links must include one active IPsec interface.
c) Overlay links must be configured with a dedicated firewall policy.
d) Overlay links must be added to a SD-WAN zone.
04. You want to configure ADVPN without route reflection on your SD-WAN topology. Which two statements apply to this scenario?
(Choose two.)
a) ADVPN without route reflection is compatible with BGP on loopback.
b) ADVPN without route reflection allows hub-side steering by route tag.
c) ADVPN without route reflection is also called ADVPN 2.0.
d) ADVPN without route reflection is compatible with static routing on the overlay.
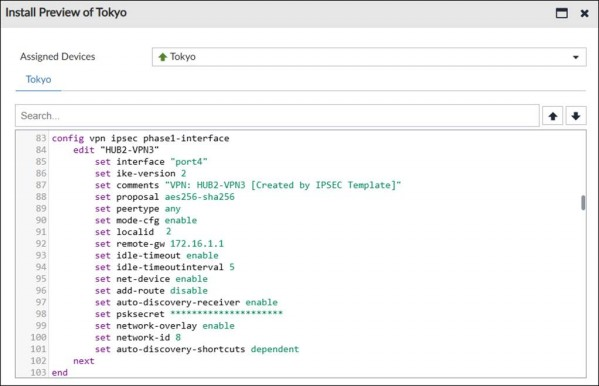
05. Refer to the exhibit.
The administrator used the SD-WAN overlay template to prepare an IPsec tunnel configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the FortiManager installation preview for one FortiGate device.
Based on the exhibit, which statement best describes the configuration applied to the FortiGate device?
a) It is a spoke device. It can trigger the establishment of an ADVPN shortcut.
b) It is a hub device. It will automatically discover the spoke devices and add them to the SD-WAN topology.
c) It is a hub device in a dual-hub topology. It can participate in the establishment of ADVPN shortcuts.
d) It is a spoke device. It can establish shortcuts only if the remote spoke initiates the request.
06. You configured a manual SD-WAN rule to steer game and social media traffic through port2. However, when analyzing the traffic flow you notice that the volume of traffic through port2 is much smaller than expected.
What should you check on the FortiGate configuration?
a) Check whether application-group detection is allowed on the firewall policy that allows the traffic flow.
b) Check on the FortiGate CLI whether the feature that allows the detection of applications per group is enabled.
c) Check whether application filter is allowed in the FortiGuard settings.
d) Check whether application control is allowed on the firewall policy that allows the traffic flow.
07. You are configuring SD-WAN zones and members on a FortiGate device. Which two facts should you take into account?
(Choose two.)
a) You can add any physical interface to a zone.
b) You can add only SD-WAN members to a zone.
c) The default zone is virtual-wan-link.
d) The default zone is sdw-default
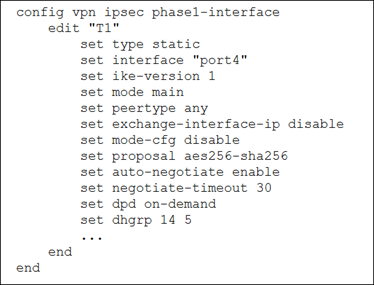
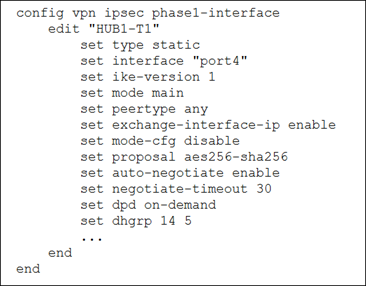
08. Refer to the exhibits.
The VPN configuration on a spoke and a hub is shown.
The administrator wants to use those tunnels to build an SD-WAN topology.
Which one parameter must you modify to allow the tunnel to come up and be used in the SD-WAN topology?
a) Set exchange-interface-ip to enable on the hub side.
b) Set mode-cfg to enable on the spoke side.
c) Set the type to dynamic on the hub side.
d) Change ike-version to 2 on the hub and the spoke.
09. Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule?
(Choose two.)
a) The session information output displays no SD-WAN service ID.
b) By default, FortiGate load balance the traffic according to the source IP address.
c) FortiGate flags the session with sdw-imp.
d) The traffic is distributed through only static routes or directly connected routes.
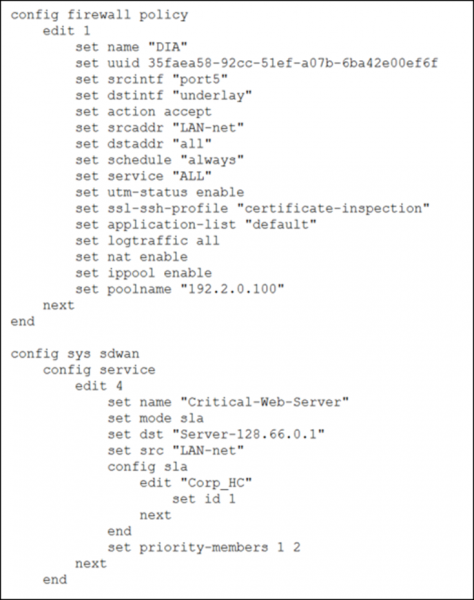
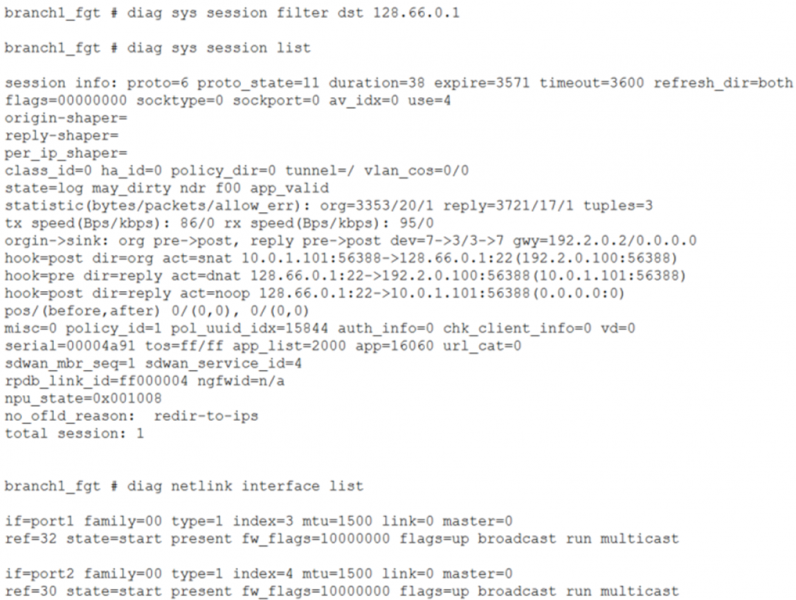
10. Refer to the exhibits.
You have configured an SD-WAN rule and a firewall policy. You check the interface list, and the sessions established between a LAN device and a server located on another side.
Based on the exhibits, if the performances of port1 falls outside SLA, what can you expect for traffic matching the session shown?
a) FortiGate will drop the session. The user must establish a new session that FortiGate will steer through port2.
b) You must check the underlay zone configuration to know the answer.
c) You must check the system global configuration to know the answer.
d) FortiGate will flag the session as dirty, and reevaluate the interface to use when the next packet arrives.
 Before you write the Fortinet SD-WAN Enterprise Administrator (NSE6_SDW_AD-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Access Service Edge (SASE) (SD-WAN Enterprise Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet SD-WAN Enterprise Administrator (NSE6_SDW_AD-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Access Service Edge (SASE) (SD-WAN Enterprise Administrator) sample questions and demo exam help you in removing these doubts and prepare you to take the test.