01. A DevOps team is using Terraform to manage their infrastructure across multiple environments. Currently, the Terraform state file is stored locally on a developer’s machine. The team decides to migrate the state file to a remote back-end machine.
Why is storing the Terraform state file in a remote location considered a best practice in this scenario?
a) It eliminates the need to define provider configurations in the state file.
b) It ensures that the state file is encrypted.
c) It enables collaboration among multiple team members.
d) It prevents the accidental deletion of the state file.
02. Refer to the exhibits.
An organization uses Terraform to manage Amazon Web Services (AWS) resources, including generating sensitive values such as access keys. To prevent the accidental exposure of these values in CLI output, the architect wants to ensure that sensitive outputs are securely managed.
How can the architect prevent sensitive outputs from being displayed in CLI output?
a) Use environment variables to mask sensitive output values.
b) Add the sensitive output values to the .gitignore file to avoid committing them to version control.
c) Use the sensitive argument in the output block for the sensitive values.
d) Encrypt the Terraform state file using AWS Key Management Service (KMS).
03. Which statement about Amazon Web Services (AWS) Transit Gateway is true for SD-WAN transit gateway (TGW) Connect with FortiGate?
a) Attaching a virtual private cloud (VPC) to the TGW automatically adds new routes to the subnet route table.
b) TGW supports BGP to share routes with FortiGate.
c) The TGW plugin must be used with a VPN to achieve higher bandwidth.
d) The Generic Routing Encapsulation (GRE)-based tunnel attachments are slower than IPsec tunnels.
04. Which two statements about the Amazon Web Services (AWS) security groups are true?
(Choose two.)
a) A security group is a stateful list of ingress and egress traffic rules
b) EC2 instances, elastic network interfaces (ENIs), and subnets may have security groups configured on them.
c) Security groups are applicable at the instance level.
d) Configured traffic rules may have an action of allow or deny.
05. You are tasked with adding public cloud accounts to FortiCNP cloud protection. After adding an Azure account, you notice the status shows as Partially running. What can you conclude from that status?
a) FortiCNP may still be able to monitor the cloud account.
b) FortiCNP detected that you are using a free Azure account.
c) FortiCNP is verifying if there are enough license seats to add the account.
d) FortiCNP will take approximately 15 minutes to change the status to Running.
06. A DevOps team is configuring Terraform to deploy Amazon Web Services (AWS) resources. They want to use environment variables to authenticate Terraform with AWS, while ensuring that the setup works across multiple developers' machines without exposing credentials in configuration files.
Which two environment variables must the team configure, at a minimum, to allow Terraform to authenticate with AWS?
(Choose two.)
a) AWS_ACCESS_KEY_ID
b) AWS_ACCOUNT_ID
c) AWS_ROLE_ARN
d) AWS_SECRET_ACCESS_KEY
07. An administrator is planning to use FortiDevSec to detect vulnerabilities in container images and is researching any platform limitations that they must take into account when using that tool. What is a limitation of FortiDevSec container security scanning?
a) It does not support scanning private images that require Docker login.
b) It focuses on scanning for encrypted secrets in containerized applications.
c) It can detect vulnerabilities in containerized applications in Amazon Web Services (AWS) environments only.
d) It is limited to dynamic application testing of container images.
08. The DevOps team is troubleshooting a FortiGate software-defined network(SDN) connector that is failing to integrate with a Kubernetes cluster. While using several debug commands, they find that the connector connection generates an error code 401. What is the cause of this error?
a) The FortiGate firewall is using HTTP to send API calls instead of HTTPS.
b) The service principal being used has the correct role assigned.
c) The configured client secret credentials are incorrect.
d) The Kubernetes cluster is using an unsupported API version.
09. Which three features are part of the FortiCNAPP modular architecture that provides deep visibility, risk management, and threat protection?
(Choose three.)
a) FortiGate
b) FortiGuard/
c) Code Security
d) FortiAnlayzer
e) FortiSOAR
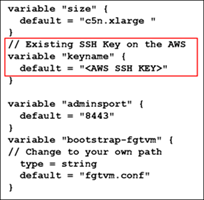
10. While working with Terraform files, an administrator notices that some of the variables do not have their type explicitly declared.
What type of variable is vpccidr in the exhibit?
a) Number
b) Map
c) Set
d) String
 Before you write the Fortinet Public Cloud Security Architect (NSE7_CDS_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Cloud Security (Public Cloud Security Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet Public Cloud Security Architect (NSE7_CDS_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Cloud Security (Public Cloud Security Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.