 Before you write the Fortinet Security Operations Architect (NSE7_SOC_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Security Operations (Security Operations Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet Security Operations Architect (NSE7_SOC_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Security Operations (Security Operations Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
The best approach to pass your Fortinet NSE7_SOC_AR-7.6 exam is to challenge and improve your knowledge. To test your learning and identify improvement areas with actual exam format, we suggest you practice with Premium Fortinet NSE7_SOC_AR-7.6 Certification Practice Exam. The practice test is one of the most important elements of your Fortinet NSE 7 - Security Operations 7.6 Architect (Security Operations Architect) exam study strategy to discover your strengths and weaknesses, to improve your time management skills and to get an idea of the score you can expect.
Fortinet NSE7_SOC_AR-7.6 (Security Operations Architect) Sample Questions:
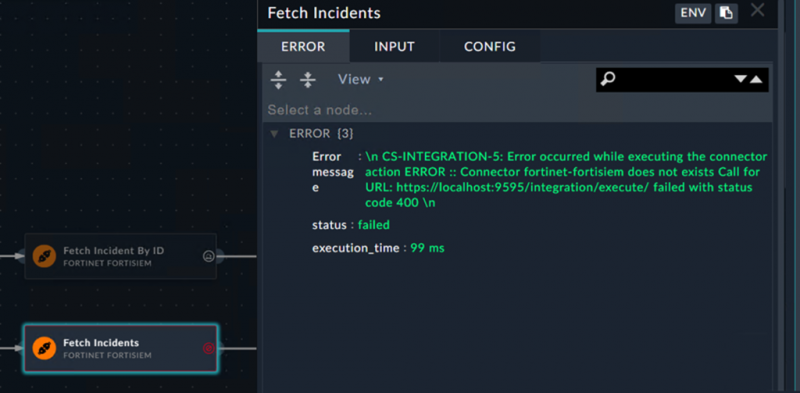
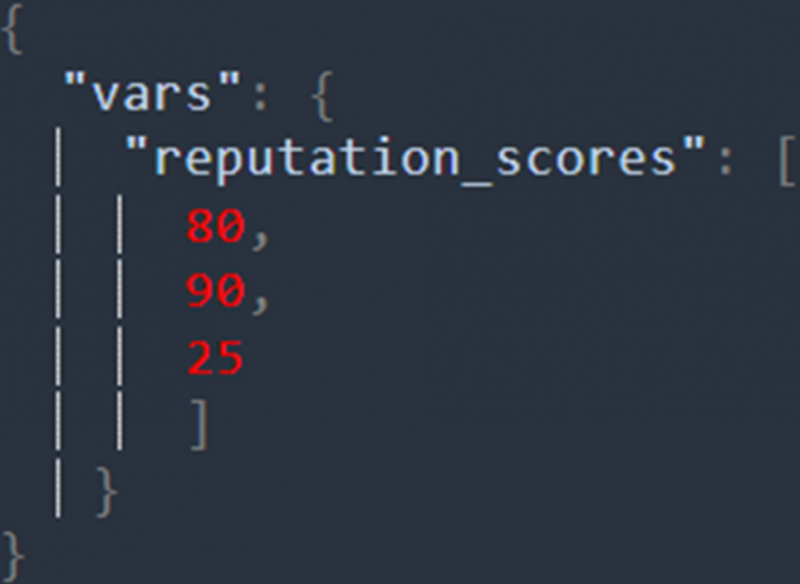
a) (( avg | vars.reputation_scores ))
Solutions:
|
Question: 01 Answer: c, d |
Question: 02 Answer: c |
Question: 03 Answer: d |
Question: 04 Answer: a |
Question: 05 Answer: b, c, e |
|
Question: 06 Answer: a |
Question: 07 Answer: b |
Question: 08 Answer: a |
Question: 09 Answer: b |
Question: 10 Answer: c |
Note: If you find any error in these Fortinet NSE 7 - Security Operations 7.6 Architect (Security Operations Architect) sample questions, you can update us by write an email on feedback@nwexam.com.
