01. Which encryption protocols can CAPWAP use to secure the data channel when communicating between a FortiGate wireless controller and FortiAP?
a) WPA3 and TLS
b) SSH and SSL
c) DTLS and IPsec
d) SSL/TLS and IPsec
02. An LDAP server has been successfully configured on FortiGate, which forwards authentication requests to a Windows Active Directory (AD) server. Users can authenticate using PAP, but authentication fails with MSCHAPv2. Why is it not recommended to use PAP for authentication?
a) PAP sends passwords in cleartext.
b) PAP requires the use of an insecure port that is easily blocked by firewalls.
c) PAP does not support domain-based authentication for Active Directory.
d) PAP is only supported for local user accounts, not external authentication sources.
03. You are configuring a new wireless network for your organization. The network requires users to authenticate through a RADIUS server for secure access. Which two security modes should you select when creating the SSID to ensure compatibility with the RADIUS server?
(Choose two.)
a) WEP
b) WPA-Personal
c) WPA3-Enterprise
d) WPA/WPA2 Mixed Mode
e) WPA2-Enterprise
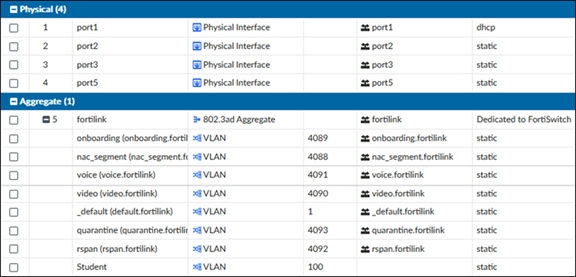
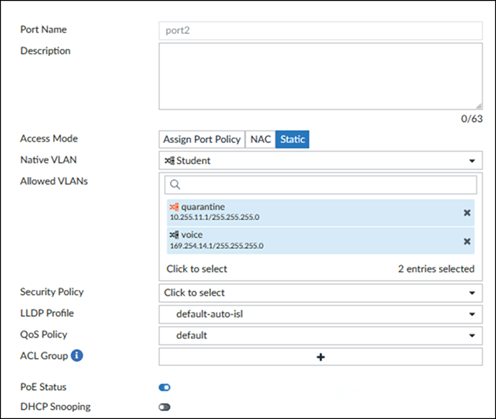
04. Refer to the exhibits which show the FortiSwitch and FortiGate interface configurations.
FortiSwitch VLAN configuration
Port2 interface configuration
Which two statements describe how port2 handles tagged and untagged traffic?
(Choose two.)
a) Port2 accepts ingress tagged traffic for VLAN IDs 4091 and 4093 only.
b) Port2 assigns ingress untagged traffic to VLAN 100.
c) Port2 accepts ingress untagged traffic for VLAN IDs 100, 4091, and 4093 only.
d) Port2 tags egress traffic for VLAN 100.
05. A network administrator wants a newly deployed FortiGate to automatically discover its FortiManager without manual configuration. Which of the following must be correctly configured for this process to work?
a) FortiGate interface administrative access must have enabled Security Fabric Connection.
b) The FortiGate interface must be set to receive an IP address over DHCP.
c) The DHCP server must provide a valid default gateway to reach FortiManager.
d) The DHCP server must include Option 240 or Option 241 in its lease offers.
06. Which features does FortiAuthenticator support when acting as a certificate authority (CA)?
a) It can issue and revoke digital certificates but cannot act as an OCSP server.
b) It can integrate with third-party certificate authorities to validate external certificates.
c) It functions solely as a CRL repository and does not support certificate signing requests (CSR).
d) It can act as a self-signer for issuing and revoking digital certificates.
07. You want to configure Syslog-based single sign-on (SSO) on FortiAuthenticator to enhance user authentication across your network. You have to ensure that the system correctly extracts the user information from syslog messages and links it to the correct authentication events.
Which two steps must you perform to successfully configure Syslog SSO on FortiAuthenticator?
(Choose two.)
a) Specify the devices that will send syslog messages to FortiAuthenticator.
b) Configure parsing rules to extract the relevant information from syslog messages.
c) Configure the syslog messages that FortiAuthenticator sends to authentication devices.
d) Set up user authentication policies in FortiAuthenticator.
e) Enable syslog forwarding on source devices.
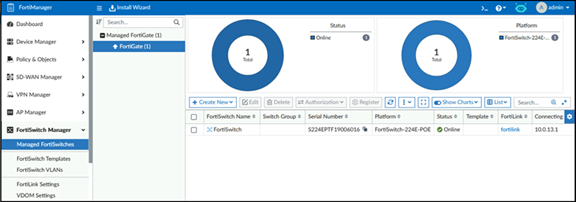
08. Refer to the exhibit.
The FortiManager device is set to central management mode for FortiSwitch devices. How are configuration changes applied to multiple FortiSwitch devices?
a) Configuration changes require manually updating each device.
b) Changes are applied only to switches that share the same model number.
c) Changes are made through a template.
d) Configuration changes are made on individual switches.
09. You need to deploy a security policy on a FortiSwitch port connected to legacy printers that do not support 802.1X authentication. How can you configure the network to ensure these printers have access while maintaining security?
a) Enable MAC Authentication Bypass (MAB) on the FortiSwitch port.
b) Configure the FortiSwitch port to operate in promiscuous mode.
c) Assign the printers to a high-priority VLAN that bypasses security policies.
d) Use port mirroring to copy traffic from the printer to another secured port for authentication.
10. Your team is planning to configure a FortiGate wireless network that automatically quarantines devices using automation stitches. Which two configurations must be in place for a wireless client to be successfully quarantined upon detecting IOC events?
(Choose two.)
a) Enable Device Detection at the interface level.
b) FortiAnalyzer must have a valid threat detection services license.
c) SSIDs must be configured in Bridge mode.
d) Configure FortiGate as a member of a Security Fabric group.
 Before you write the Fortinet LAN Edge Architect (FCSS_LED_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Networking (LAN Edge Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.
Before you write the Fortinet LAN Edge Architect (FCSS_LED_AR-7.6) certification exam, you may have certain doubts in your mind regarding the pattern of the test, the types of questions asked in it, the difficulty level of the questions and time required to complete the questions. These Fortinet Certified Solution Specialist - Secure Networking (LAN Edge Architect) sample questions and demo exam help you in removing these doubts and prepare you to take the test.